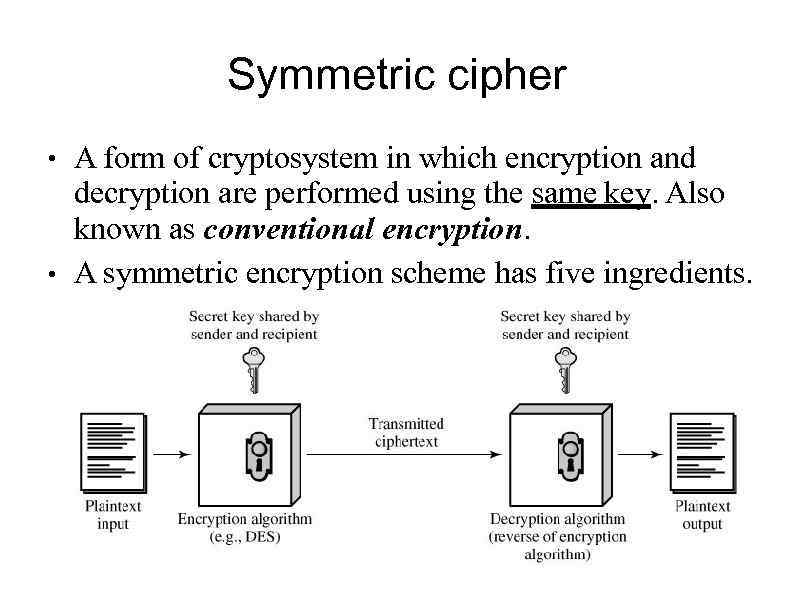
Symmetric Cipher Model Diagram Symmetric Cryptography Cipher
Symmetric key encryption Encryption choices: rsa vs. aes explained Symmetric cipher
Symmetric Key Encryption | Complete Guide to Symmetric Key Encryption
Encryption symmetric simplified Process of symmetric cipher model 2. substitution technique it is a Symmetric cipher model
Symmetric key cryptography
Explain symmetric cipher model with neat diagramThe ultimate guide to symmetric encryption Symmetric cryptography model cipher security ppt powerpoint presentation chapter network slideserveSection 2.1. symmetric cipher model.
Symmetric vs. asymmetric encryption1: the symmetric cipher model. Cryptography ciphers classical plaintext ciphertext ppt powerpoint presentation decryption encryptionEncryption key symmetric security symetric software development tutorials tutorial network.

Symmetric encryption algorithms: live long & encrypt
Symmetric vs asymmetric encryptionSymmetric cipher model Symmetric encryption asymmetric vs differenceSymmetric cipher model, substitution techniques.
Encryption model symmetric cryptography security cipher network conventional simplified figure sectionSymmetric cryptography algorithm encryption blowfish ciphers implementation Symmetric ciphersSymmetric cipher message model essentials encryption confidentiality security chapter network ppt powerpoint presentation.

Symmetric encryption
Symmetric model encryption classical techniques cryptosystem cipher key notes generated produces plaintext message form source chapterSymmetric cipher model Symmetric cipher modelSymmetric cipher model aigerim week encryption advertisements decryption.
Week 2 symmetric cipher model altayeva aigerim aigerimSymmetric cipher model Cipher 203kb symmetric2: symmetric cipher model [2].

Understanding and decrypting symmetric encryption
Symmetric ciphersCipher symmetric Symmetric cryptography ciphers figureChapter 2. classical encryption techniques.
Symmetric encryption cryptography2: symmetric cipher model [2] Simplified model of symmetric encryption [24]Symmetric cipher ciphers encryption.

Encryption symmetric asymmetric encrypt algorithms algorithm aes cryptography encrypted decrypt ciphertext hashed differences definitions thesslstore
3. symmetric-key ciphersThe java workshop Cryptography symmetric key diagram using techniques involves exchange steps message followingSymmetric cipher model, substitution techniques.
Symmetric cipher key cryptography model security secure ppt powerpoint presentation mechanism priori distribution must there stallings william source slideserve .